IAM Roles, Temporary Credentials & Alerting - AWS Well-Architected Framework (Security Pillar)
Source: Dev.to
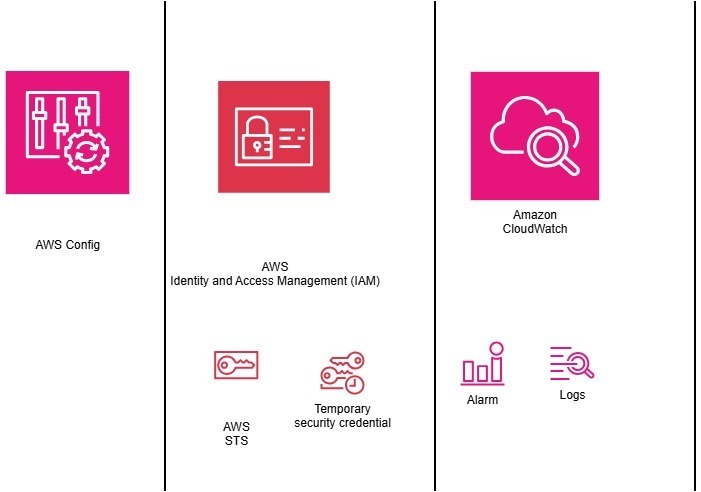
Strong Identity Foundations (IAM Roles)
Designed a least‑privilege IAM role for an EC2‑based application, granting read‑only access to S3 and eliminating long‑term static credentials.
Short‑Lived Access with AWS STS
Used AWS Security Token Service (STS) to assume roles and generate temporary credentials, significantly reducing credential exposure and blast radius.
Explicit Trust Relationships
Defined precise trust policies to control who can assume roles—ensuring access is intentional, secure, and auditable.
Continuous Monitoring & Alerting
Configured CloudWatch alarms backed by AWS Config metrics to detect IAM user creation, modification, or deletion in near real time.
Summary Diagram
Key Takeaway
Security starts with identity. Short‑lived credentials, least privilege, and real‑time alerting are core principles of the AWS Well‑Architected Security Pillar.
Hashtags: #AWSWellArchitected #SecurityPillar #IAM #STS #CloudSecurity