I Built an Open-Source Cowork in 24 Hours with ZERO Rust Experience — and the Agent Builts Itself
Source: Dev.to
I walked into this with exactly zero Rust experience and a stubborn belief: building an agent shouldn’t require a megachurch of frameworks. Twenty‑four hours later, I shipped a Rust‑native AI Agent desktop for non‑devs that compiled to a 16 MB binary, a simple while loop with Skills, MCPs supported, BYOK (Bring Your Own Key) and even local models!
The Stack
- Rust – from zero to shipping in one day
- Long‑term memory – file system as persistent, queryable context
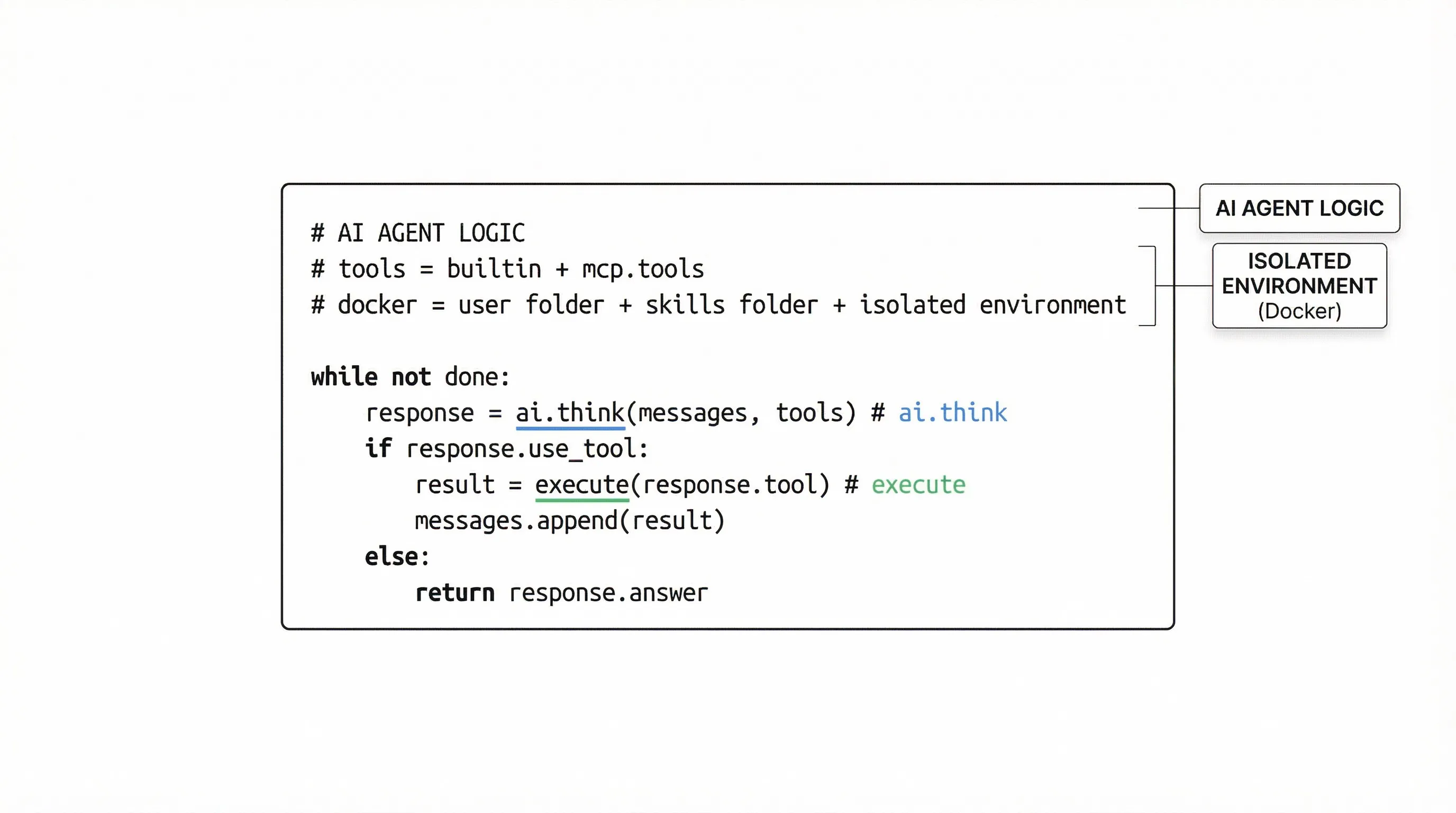
- Loop – a single
whileloop coordinating I/O and tool calls - Tools – built‑in file tools (read, write, bash) + MCP‑compliant providers (extensible)
- Sandboxing – a simple Docker container isolates most risks
Secret Sauce
- Keep state in plain files and directories.
- Keep orchestration in a simple loop, not a framework.
- Teach the AI to read and write its own operating context, in files.
What I Learned
1. You don’t need an agent framework
Frameworks often add unnecessary abstraction and complexity. A simple loop suffices:
- Observe – read inputs, logs, and task files
- Decide – ask the model for the next atomic action
- Act – call a tool (MCP) or write to disk
- Reflect – append outcomes to a local journal
2. The file system is all you need
Vector stores and RAG farms are great, but they can become speculative overhead.
- Everything as files: tasks, plans, diffs, decisions, and logs live as plain text or JSON.
- Modern RL‑trained models work well with Linux file systems.
- Using the FS as “long‑term memory” makes persistence trivial and recoverability obvious.
3. The surreal mirror: AI coding reproduces itself
I used an AI agent (Claude Code) to help build the project. The Open Cowork is essentially a GUI with a Copilot‑like agent behind it, showing how an AI can reproduce itself in Rust.
4. Security as a first‑class citizen
Agents are powerful, but without boundaries they become liabilities. For non‑devs, security isn’t just a feature—it’s the foundation.
- Hard sandboxing (e.g., Docker) and strict whitelisting of system commands or network calls keep the agent helpful, not a system threat.
Code Overview
The entire codebase can be summarized in the loop below:
The project is open source:
Feel free to explore, try it out, and share any feedback!