Understanding Red Team Operations: A Technical Deep Dive
Source: Dev.to
Originally published at Cyberpath
What is Red Teaming?
Red teaming goes beyond traditional penetration testing by simulating real‑world adversaries to test an organization’s detection and response capabilities.
Unlike pentesting, which focuses on finding vulnerabilities, a red‑team engagement evaluates the entire security program. It assesses not only technical controls but also people, processes, and the organization’s ability to detect and respond to sophisticated attacks over an extended period.
Red Team Engagement Phases
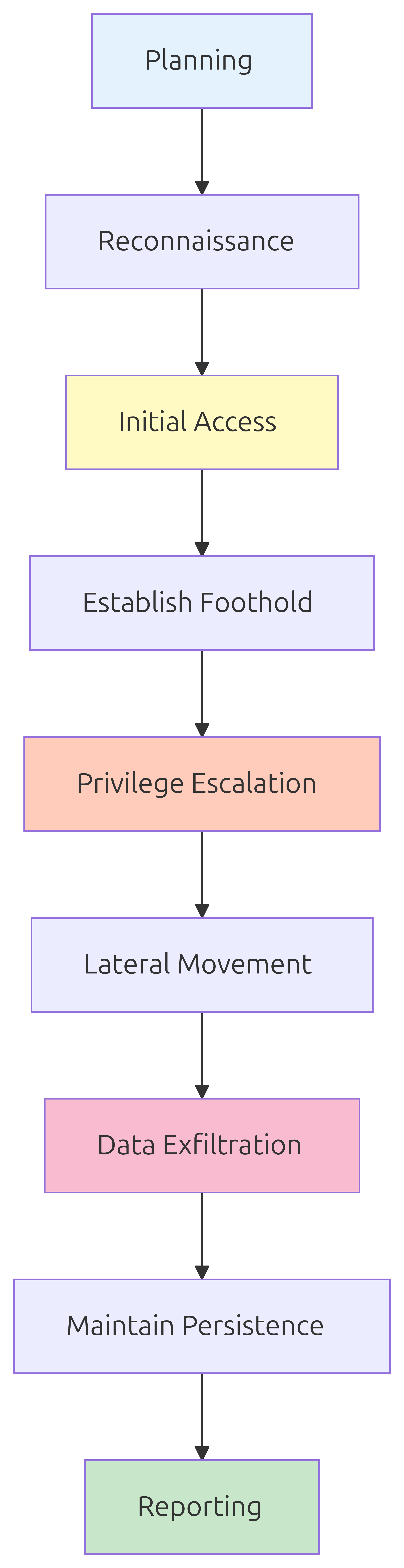
Phase 1: Reconnaissance
Reconnaissance is the foundation of any successful red‑team operation. Professional red‑teamers spend significant time gathering intelligence about their target before attempting any active engagement. This phase involves:
- Collecting information from publicly available sources.
- Analyzing the target’s digital footprint.
- Building a comprehensive understanding of the attack surface.
OSINT (Open Source Intelligence)
Open‑source intelligence gathering leverages publicly available information to build a profile of the target organization:
| Source | What It Reveals |
|---|---|
| Company websites | Technology stacks, employee names, organizational structure |
| Job postings | Internal tools, technologies, security practices |
| Social media | Employee relationships, potential social engineering vectors |
| DNS records & subdomain enumeration | Extent of internet‑facing infrastructure |
| Public code repositories | Sensitive data such as API keys or architectural details |
| Data‑breach databases | Previously compromised credentials that could provide initial access |
Phase 2: Initial Access
After gathering intelligence, the next step is to gain initial access. The chosen attack vector depends on the target’s security posture and the rules of engagement.
- Phishing – Crafted emails that trick users into providing credentials or executing malicious payloads (MITRE Phishing).
- Web‑application exploitation – Targeting vulnerabilities such as SQL injection, cross‑site scripting (XSS), or remote code execution.
- Credential stuffing – Leveraging leaked credentials from previous breaches.
- Social engineering – Manipulating individuals to divulge confidential information or perform insecure actions.
- Physical access attacks – Gaining unauthorized entry to facilities or direct access to devices.
- Supply‑chain compromises – Targeting third‑party vendors or service providers to gain indirect access to the target organization.
Phase 3: Command and Control (C2)
After initial access, a command‑and‑control (C2) channel must be established.
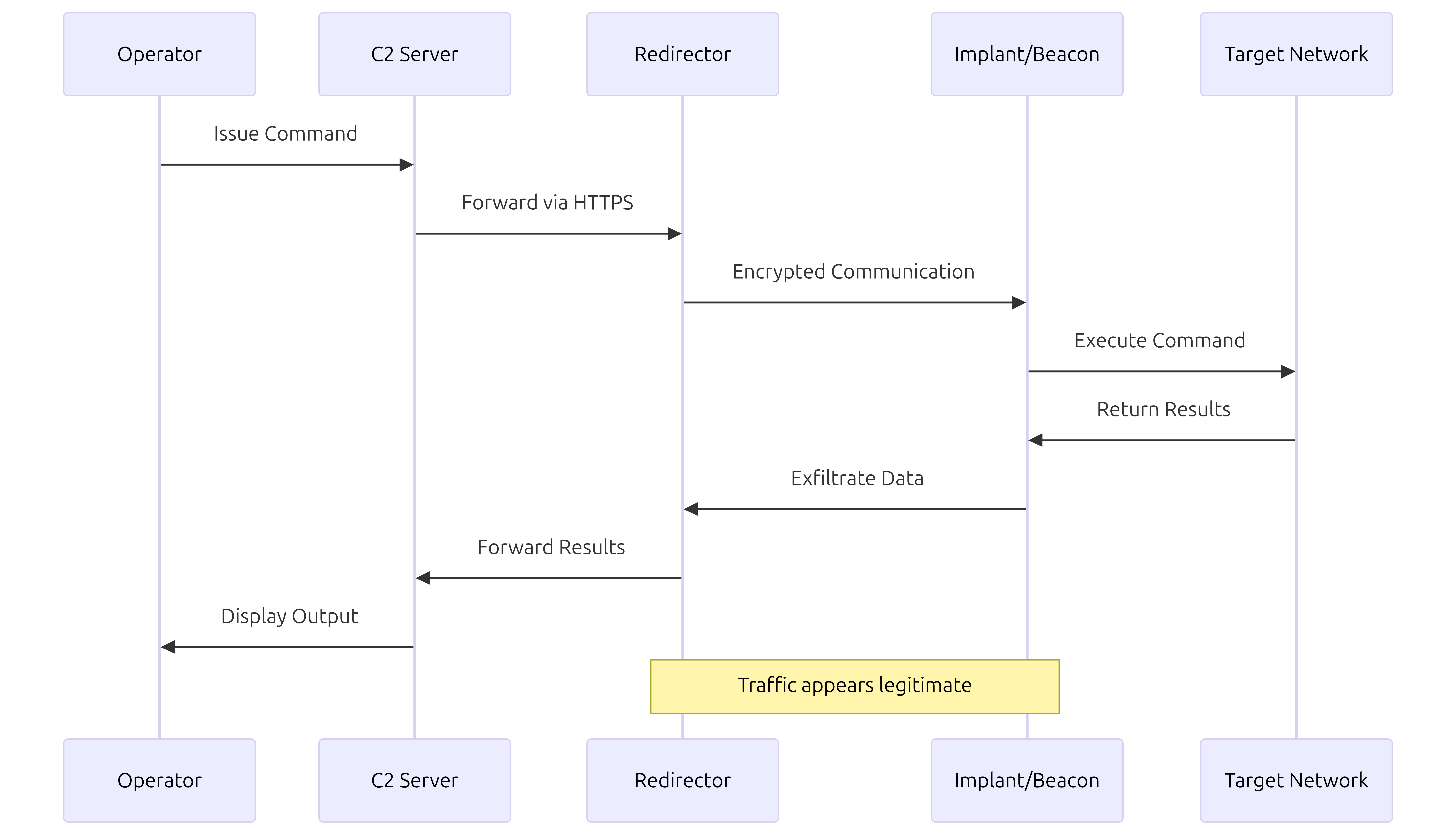
C2 Evasion Techniques
Modern red‑team operations use sophisticated techniques to avoid detection by security monitoring systems:
- Domain fronting – Hides the true destination of traffic behind trusted CDN services, making it appear as legitimate traffic to major cloud providers.
- DNS tunneling – Exfiltrates data through DNS queries, bypassing many network controls.
- Encrypted payloads & custom protocols – Prevent deep‑packet inspection from revealing malicious activity.
- Living‑off‑the‑land binaries (LoLBins) – Leverages legitimate system utilities to perform malicious actions, reducing the likelihood of triggering alerts.
- Beaconing randomization – Varies timing and size of C2 communications to blend in with normal traffic patterns.
- Protocol mimicry – Makes C2 traffic look like legitimate protocols such as HTTPS or DNS, blending in with normal network activity.
- Time‑based execution – Communicates primarily during business hours when network activity is highest, reducing detection chances.
- Jitter & randomized sleep intervals – Prevent security systems from identifying regular beacon patterns that indicate compromised hosts.
Phase 4: Privilege Escalation
After establishing access, elevated privileges are typically required. Common Windows privilege‑escalation techniques include:
| Technique | Description | Difficulty |
|---|---|---|
| Token Impersonation | Steal access tokens from privileged processes | Medium |
| UAC Bypass | Circumvent User Account Control | Easy‑Medium |
| Service Misconfigurations | Abuse weak service permissions | Easy |
| DLL Hijacking | Place malicious DLL in a search path | Medium |
| Scheduled Tasks | Exploit weak scheduled‑task permissions | Easy‑Medium |
Phase 5: Lateral Movement
Once privileged access is obtained on one system, the team moves laterally across the network:
Red Team vs. Blue Team
Understanding both sides makes you a better security professional.
- Red teams simulate real attackers to find vulnerabilities before malicious actors do, test detection and response capabilities, and challenge assumptions about security controls. They operate with an offensive mindset, constantly probing technical controls, processes, and human factors.
- Blue teams monitor and defend systems, detect and respond to threats, implement security controls, and learn from red‑team findings. They maintain a defensive posture, continuously improving detection capabilities and response procedures based on real incidents and red‑team exercises.
The interaction between red and blue teams creates a feedback loop that strengthens the overall security posture.
Essential Red Team Tools
Professional red‑teamers rely on a curated toolset covering every phase of an engagement.
| Phase | Tool | Description |
|---|---|---|
| Reconnaissance | Nmap | Network scanning and service detection |
| Masscan | High‑speed port scanning | |
| Amass | Subdomain enumeration | |
| theHarvester | Automated OSINT gathering from multiple sources | |
| Initial Access | Metasploit | Comprehensive exploitation framework |
| Cobalt Strike | Commercial C2 platform with advanced evasion features | |
| Gophish | Realistic phishing‑campaign simulation | |
| SET – Social Engineering Toolkit | Automation of a wide range of social‑engineering attacks | |
| Post‑Exploitation | Mimikatz | Credential extraction from Windows systems |
| BloodHound | Graph‑based analysis of Active Directory relationships and privilege‑escalation paths |
Feel free to expand the list with additional tools that fit your workflow.
Tools Overview
- BloodHound – visualizes Active Directory attack paths.
- PowerSploit – a collection of PowerShell post‑exploitation modules.
- Empire – provides PowerShell and Python post‑exploitation capabilities with a user‑friendly interface.
- SharPersist – a Windows persistence toolkit for maintaining footholds.
- Impacket – implements network protocols useful for lateral movement.
- Covenant – a .NET‑based C2 framework that emphasizes operational security.
Best Practices for Red Team Operations
Professional red‑team engagements require strict adherence to ethical and operational guidelines:
- Obtain proper authorization – secure written, signed agreements before any testing begins.
- Define clear Rules of Engagement (RoE) – specify in‑scope and out‑of‑scope systems, timeframes, and acceptable techniques.
- Maintain operational security – protect client data and engagement details from disclosure.
- Document everything – keep detailed logs of actions for reporting and legal protection.
- Communicate responsibly – report critical findings immediately rather than waiting for the final report, especially for actively exploited vulnerabilities.
- Clean up after yourself – remove persistence mechanisms, backdoors, and any artifacts created during testing.
- Provide actionable remediation guidance – help the client fix identified issues, not just list problems.
Remember: the goal is to improve security, not merely to showcase technical prowess.
Conclusion
Red‑team operations are complex, multifaceted engagements that demand deep technical knowledge, creativity, and ethical responsibility. By simulating sophisticated adversaries, red teams help organizations understand their true security posture and strengthen their defensive capabilities.
Professional red teaming goes beyond finding vulnerabilities; it tests the entire security program—including people, processes, and technology. The insights gained enable organizations to prioritize security investments, enhance detection capabilities, and build more resilient systems. Ultimately, red teaming is about improving security through adversarial simulation, preparing organizations for the real threats they will inevitably face.
Further Reading
- MITRE ATT&CK Framework – comprehensive documentation of adversary tactics and techniques observed in real‑world attacks.
- Red Team Development and Operations – practical guidance for conducting professional engagements.
- Awesome Red Teaming – a curated repository of tools, resources, and learning materials.
- Red Teaming Handbook (PDF) – covers planning and executing engagements from initial scoping through final reporting.
